Product
Learn more about the all-in-one, most powerful solution for community engagement

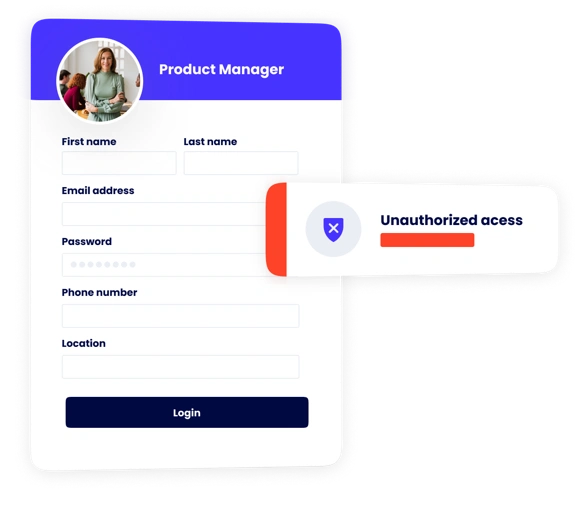
We employ industry-leading AES-256 encryption for data at rest and in transit. This advanced encryption algorithm ensures that your sensitive data remains protected from unauthorized access.
Our software development process follows a rigorous and secure lifecycle. We conduct comprehensive security and privacy checks, along with stringent quality assurance practices, to identify and address any vulnerabilities before deployment.

We are proud to hold the prestigious ISO27001 certification, which underscores our commitment to implementing and maintaining robust information security management systems. Additionally, our adherence to the Payment Card Industry Data Security Standard (PCI-DSS) certification demonstrates our dedication to secure payment processing.
Regular and thorough penetration testing is conducted by qualified security professionals to identify potential vulnerabilities. We also perform continuous internal and external vulnerability assessments to proactively detect and remediate any security weaknesses.

We strictly adhere to the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA-CPRA) to protect your privacy rights and ensure the lawful handling of personal data.
Our robust Web Application Firewall provides an additional layer of protection, shielding your data from potential threats and unauthorized access attempts.